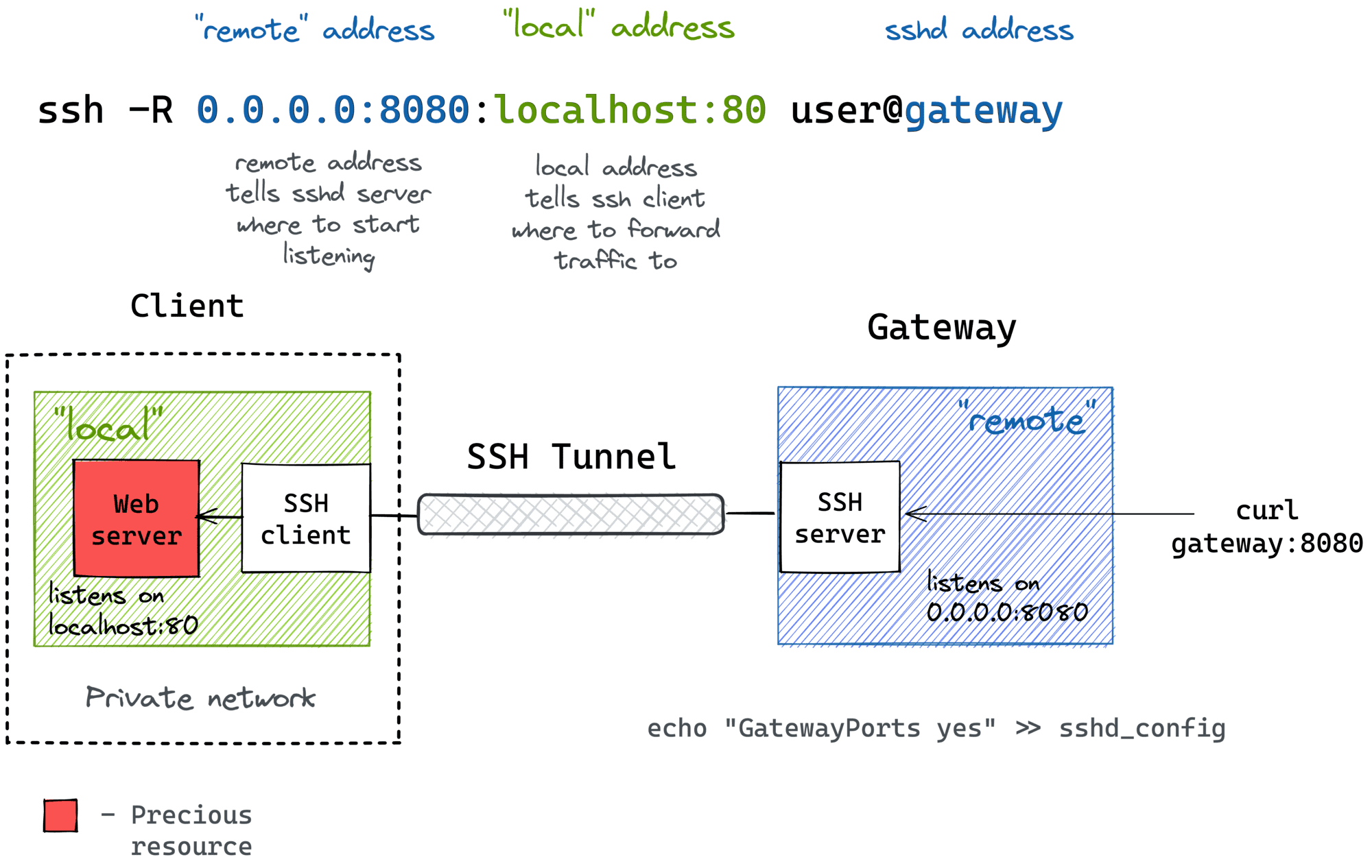
SSH Remote IoT Example has become a buzzword in the tech world, especially for those who want to secure their IoT devices. As the Internet of Things continues to grow, the need for secure communication between devices is more important than ever. Imagine having the ability to remotely control your smart home system or monitor industrial equipment from anywhere in the world—all while keeping your data safe. That’s exactly what SSH offers, and we’re here to break it down for you in the simplest terms possible. So buckle up, because we’re diving deep into the world of SSH and IoT!
Now, let’s face it—IoT devices are everywhere. From smart fridges to wearable fitness trackers, these gadgets have transformed the way we live and work. But with great power comes great responsibility, right? Securing these devices is no longer optional; it’s a necessity. That’s where SSH comes in. Short for Secure Shell, SSH is like the superhero of remote connections, protecting your IoT setup from hackers and cyber threats. In this guide, we’ll show you how to use SSH for IoT and give you some real-world examples that’ll make you a pro in no time.
Whether you’re a tech enthusiast, a developer, or just someone curious about how secure remote connections work, this article is for you. We’ll cover everything from the basics of SSH to advanced configurations, all with a focus on IoT. So grab a coffee, sit back, and let’s get started on this SSH adventure!
Read also:Christina Haack Opens Up About Tarek El Moussa The Raw Truth Behind Their Past
What is SSH and Why Should You Care?
Let’s start with the basics. SSH stands for Secure Shell, and it’s basically a protocol that allows you to securely connect to a remote device or server over an unsecured network. Think of it as a secret tunnel that lets you communicate with your IoT devices without anyone eavesdropping. But why should you care about SSH, you ask? Well, in today’s digital landscape, security is king. With cyberattacks on the rise, protecting your IoT devices is crucial—and SSH is one of the best tools for the job.
How SSH Works: A Simple Explanation
Okay, so how exactly does SSH work? Picture this: you’ve got a smart thermostat at home, and you want to adjust the temperature while you’re at work. Without SSH, anyone could potentially intercept your commands and mess with your settings. But with SSH, your commands are encrypted, making it nearly impossible for hackers to access your data. SSH uses something called public-key cryptography, which is like a digital handshake that ensures only authorized users can access the device.
Here’s the kicker: SSH doesn’t just encrypt your data—it also authenticates both the client and the server. This means that not only are your commands safe, but you’re also sure that you’re talking to the right device. Cool, right?
SSH Remote IoT Example: Real-World Applications
Now that you know what SSH is, let’s talk about how it applies to IoT. SSH remote IoT examples are everywhere, and they’re revolutionizing the way we interact with smart devices. Whether you’re managing a fleet of drones or controlling a smart irrigation system, SSH can help you do it securely. Here are a few examples to get you inspired:
- Smart Home Automation: Use SSH to remotely control your smart home devices, from lighting to security cameras.
- Industrial IoT: Monitor and manage industrial equipment, such as sensors and robots, from anywhere in the world.
- Agriculture IoT: Control irrigation systems and monitor soil conditions using SSH to ensure optimal crop growth.
- Healthcare IoT: Securely access medical devices and patient data without compromising privacy.
These examples barely scratch the surface of what SSH can do for IoT. The possibilities are endless, and as technology continues to evolve, so will the applications of SSH in the IoT space.
Setting Up SSH for IoT: Step-by-Step Guide
Ready to set up SSH for your IoT devices? Great! Here’s a step-by-step guide to help you get started:
Read also:The Neighborhood Is It Really Over All The Details
Step 1: Install SSH on Your IoT Device
First things first, you’ll need to install an SSH server on your IoT device. Most modern IoT devices come with SSH pre-installed, but if yours doesn’t, you can easily add it. For example, if you’re using a Raspberry Pi, you can enable SSH by running the following command:
sudo raspi-config
From there, navigate to the SSH option and enable it. Simple as that!
Step 2: Generate SSH Keys
Next, you’ll want to generate SSH keys for authentication. This is where the public-key cryptography magic happens. To generate keys, use the following command:
ssh-keygen -t rsa -b 4096
This will create a pair of keys: a public key and a private key. The public key goes on the IoT device, while the private key stays on your computer. Think of it like a lock and key—only the person with the private key can unlock the device.
Step 3: Connect to Your IoT Device
Once your keys are set up, it’s time to connect to your IoT device. Open your terminal and type the following command:
ssh username@device_ip_address
Replace "username" with the actual username of your IoT device and "device_ip_address" with its IP address. If everything is set up correctly, you should now be connected to your device securely!
Common SSH Commands for IoT
Now that you’re connected, here are some common SSH commands that’ll come in handy for managing your IoT devices:
- ssh-copy-id: Copies your public key to the IoT device for authentication.
- scp: Securely copies files between your computer and the IoT device.
- ssh -p: Connects to a device on a specific port.
- ssh -i: Specifies the private key to use for authentication.
These commands are just the tip of the iceberg, but they’ll get you started on managing your IoT devices like a pro.
Best Practices for SSH in IoT
Setting up SSH is one thing, but using it securely is another. Here are some best practices to keep in mind:
1. Use Strong Passwords
Even though SSH uses public-key authentication, it’s still a good idea to use strong passwords as an additional layer of security. Avoid using common words or easily guessable combinations.
2. Disable Password Authentication
Once you’ve set up public-key authentication, consider disabling password authentication altogether. This will make it much harder for hackers to brute-force their way into your device.
3. Keep Your Software Up-to-Date
Regularly update your IoT devices and SSH software to ensure you have the latest security patches. Outdated software is a hacker’s dream, so stay on top of updates!
SSH vs Other Protocols: Which One Wins?
When it comes to securing IoT devices, SSH isn’t the only game in town. There are other protocols like HTTPS and MQTT that also offer secure communication. So, how does SSH stack up against the competition?
SSH Advantages
- Highly secure due to encryption and authentication.
- Easy to set up and use.
- Compatible with a wide range of devices.
SSH Disadvantages
- May not be suitable for real-time data transfer.
- Can be resource-intensive on low-power devices.
Ultimately, the choice of protocol depends on your specific use case. For most IoT applications, SSH strikes a good balance between security and usability.
SSH Security Tips for IoT Devices
Securing your IoT devices with SSH is just the beginning. Here are some additional tips to keep your setup safe:
1. Use a Firewall
Set up a firewall to control incoming and outgoing traffic to your IoT devices. This will help prevent unauthorized access and protect your network from attacks.
2. Monitor Logs
Regularly check your SSH logs for any suspicious activity. If you notice failed login attempts or unusual connections, investigate them immediately.
3. Limit User Access
Only grant SSH access to trusted users. Avoid using shared accounts and ensure each user has their own credentials.
Future Trends in SSH and IoT
As technology continues to evolve, so will the role of SSH in IoT. Here are a few trends to watch out for:
1. Quantum Computing
With the rise of quantum computing, traditional encryption methods may become obsolete. Researchers are already working on quantum-resistant algorithms to ensure SSH remains secure in the future.
2. Edge Computing
Edge computing is all about processing data closer to the source, reducing latency and improving performance. SSH will play a key role in securing these edge devices and ensuring seamless communication.
3. AI Integration
Artificial intelligence is being integrated into IoT systems to enhance automation and decision-making. SSH will be crucial in securing these AI-powered devices and ensuring data integrity.
Conclusion: Secure Your IoT Future with SSH
And there you have it—your ultimate guide to SSH remote IoT examples! From understanding the basics of SSH to setting it up for your IoT devices, we’ve covered everything you need to know to secure your smart gadgets. Remember, security is not a one-time thing—it’s an ongoing process. Stay vigilant, follow best practices, and keep your devices up-to-date to protect them from cyber threats.
So, what are you waiting for? Dive into the world of SSH and IoT, and start building a safer, smarter future. Don’t forget to share this article with your friends and leave a comment below if you have any questions or feedback. Happy SSH-ing!
Table of Contents
- What is SSH and Why Should You Care?
- How SSH Works: A Simple Explanation
- SSH Remote IoT Example: Real-World Applications
- Setting Up SSH for IoT: Step-by-Step Guide
- Common SSH Commands for IoT
- Best Practices for SSH in IoT
- SSH vs Other Protocols: Which One Wins?
- SSH Security Tips for IoT Devices
- Future Trends in SSH and IoT
- Conclusion: Secure Your IoT Future with SSH