When it comes to managing IoT devices securely, accessing them through SSH on AWS is one of the most powerful techniques out there. In today’s digital world, where devices are interconnected like never before, ensuring secure communication is not just important—it’s critical. Imagine having full control over your IoT devices from anywhere in the world, all while keeping hackers at bay. That’s exactly what this guide is about.
Whether you're a developer, system admin, or just someone curious about how IoT works with AWS, this article will walk you through everything you need to know. We’ll cover the basics, advanced setups, and even some pro tips to make sure your IoT devices stay safe and sound.
So grab a cup of coffee, sit back, and let’s dive into the world of SSH on AWS for IoT devices. By the end of this, you’ll be ready to take on any challenge that comes your way.
Read also:Tom Selleck Opens Up About Potential Cameo In Donnie Wahlbergs Boston Blue
Table of Contents
- What is SSH and Why Use It?
- An Overview of IoT and Its Challenges
- How AWS Fits into IoT
- Setting Up SSH on AWS for IoT Devices
- Security Best Practices for IoT SSH on AWS
- Common Issues and How to Fix Them
- Scalability Considerations
- Tools and Resources for Managing IoT SSH on AWS
- Real-World Examples of IoT SSH on AWS
- Wrapping It All Up
What is SSH and Why Use It?
SSH, or Secure Shell, is like a superpower for remotely accessing devices. It’s basically a protocol that lets you connect to another computer or device over a network in a secure way. Think of it as a secret tunnel that only you can use to communicate with your IoT devices.
Now, why would you want to use SSH for IoT devices? Well, here are a few reasons:
- It’s secure as heck—SSH encrypts all your data so no one can snoop around.
- You can control devices from anywhere, as long as you have an internet connection.
- It’s super reliable and works with pretty much any device that supports it.
And when you combine SSH with AWS, you get a setup that’s not only secure but also scalable and easy to manage. But more on that later.
An Overview of IoT and Its Challenges
The Internet of Things (IoT) is basically a fancy term for all those smart devices that talk to each other. From your smart fridge to industrial sensors, IoT is everywhere. But with great power comes great responsibility, right?
Key Challenges in IoT
Managing IoT devices isn’t all sunshine and rainbows. Here are some of the biggest challenges:
Read also:Simple Ways To Boost Your Energy And Beat Fatigue
- Security: With so many devices connected, there’s a higher risk of cyberattacks.
- Scalability: As your network grows, managing all those devices can get messy.
- Connectivity: Devices need to stay connected all the time, which can be tricky in certain environments.
That’s where AWS comes in, offering solutions to these challenges and more. Let’s take a closer look.
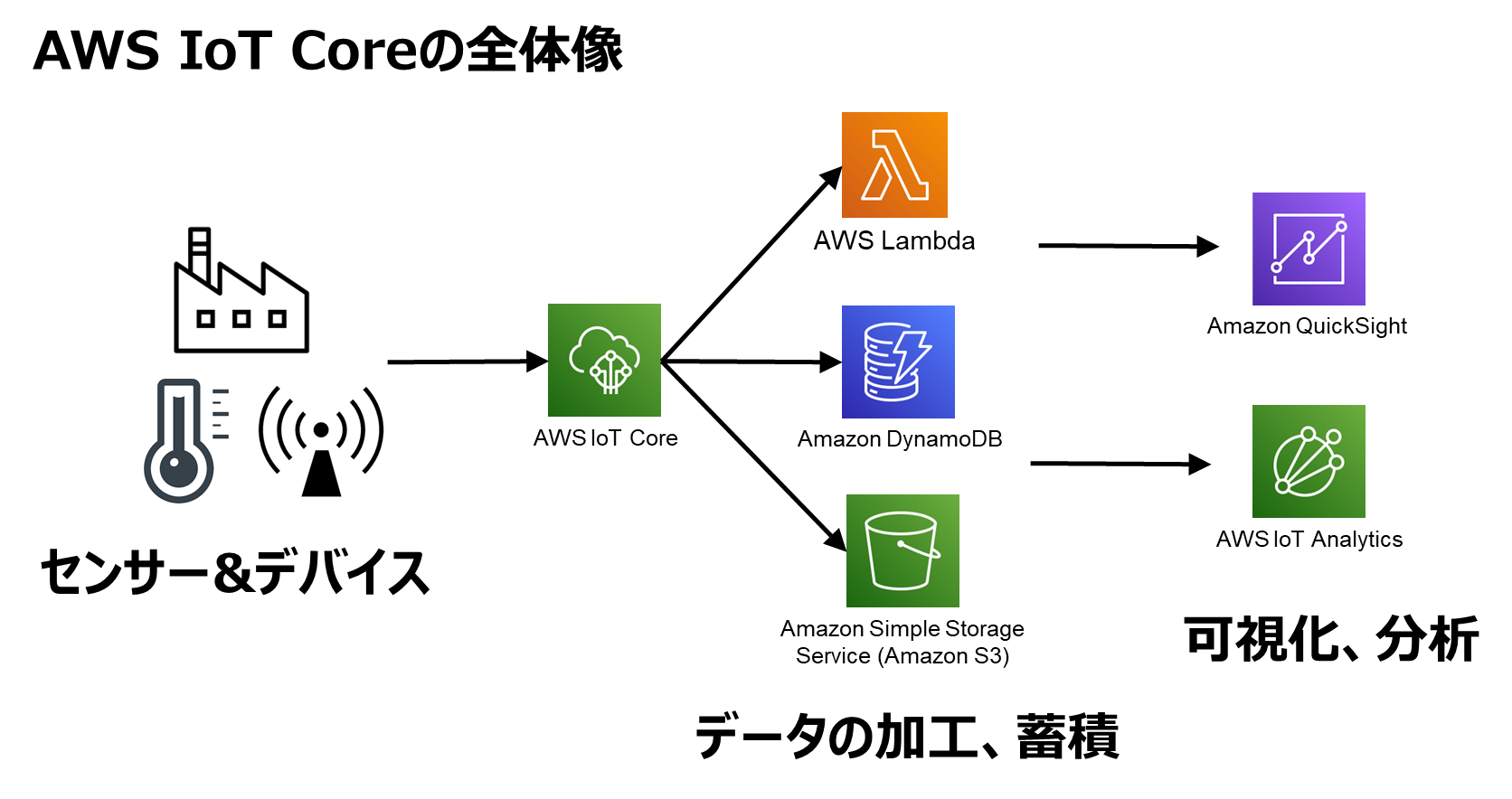
How AWS Fits into IoT
AWS IoT Core is like the Swiss Army knife for managing IoT devices. It’s a fully managed service that lets you easily and securely interact with billions of devices. Here’s how it works:
- Device Management: AWS helps you keep track of all your devices, making sure they’re up-to-date and secure.
- Secure Communication: With built-in encryption and authentication, AWS ensures your data stays safe.
- Scalability: Whether you have 10 devices or 10,000, AWS can handle it all without breaking a sweat.
And when you add SSH into the mix, you’ve got a setup that’s not only secure but also super flexible. Let’s see how to set it up.
Setting Up SSH on AWS for IoT Devices
Alright, let’s get our hands dirty and set up SSH on AWS for your IoT devices. Here’s a step-by-step guide:
Step 1: Create an EC2 Instance
First things first, you’ll need an EC2 instance to act as your SSH server. Go to the AWS Management Console, select EC2, and click on "Launch Instance." Choose an AMI that supports SSH, like Amazon Linux.
Step 2: Configure Security Groups
Security groups are like firewalls for your EC2 instance. Make sure to allow SSH traffic (port 22) so you can connect to your instance securely.
Step 3: Connect to Your Instance
Once your instance is up and running, you can connect to it using an SSH client. On Linux or macOS, you can use the terminal. On Windows, you might want to use PuTTY.
Here’s an example command:
ssh -i /path/to/your/key.pem ec2-user@your-instance-public-dns
Step 4: Secure Your SSH Setup
Don’t just stop at the basics. Here are a few tips to make your SSH setup even more secure:
- Disable password authentication and use key pairs instead.
- Change the default SSH port to something less obvious.
- Use tools like fail2ban to block malicious login attempts.
With these steps, you’ll have a secure SSH connection to your IoT devices in no time.
Security Best Practices for IoT SSH on AWS
Security should always be top of mind when working with IoT devices. Here are some best practices to keep your setup safe:
- Use Strong Authentication: Always use key pairs instead of passwords for SSH authentication.
- Regularly Update Devices: Keep your devices and software up-to-date to protect against vulnerabilities.
- Monitor Activity: Keep an eye on your logs to detect any suspicious activity.
- Limit Access: Only give SSH access to those who absolutely need it.
By following these practices, you’ll significantly reduce the risk of security breaches.
Common Issues and How to Fix Them
Even with the best setup, things can go wrong. Here are some common issues you might encounter and how to fix them:
Issue 1: Can’t Connect to SSH
Make sure your security groups are configured correctly and that your key pair is valid. Double-check your command syntax too.
Issue 2: Slow Connection
This could be due to network issues or high server load. Try optimizing your network settings or scaling up your instance.
Issue 3: Security Breach
If you suspect a breach, immediately change your key pairs and investigate your logs to find out what happened.
These fixes should help you get back on track in no time.
Scalability Considerations
As your IoT network grows, you’ll need to think about scalability. Here are a few things to consider:
- Instance Types: Choose the right instance type for your needs. Don’t overpay for resources you don’t need.
- Auto Scaling: Use AWS Auto Scaling to automatically adjust the number of instances based on demand.
- Load Balancing: Distribute traffic evenly across your instances to prevent overload.
By planning for scalability from the start, you’ll be able to handle growth without any hiccups.
Tools and Resources for Managing IoT SSH on AWS
There are tons of tools and resources available to help you manage your IoT SSH setup on AWS. Here are a few of our favorites:
- AWS IoT Core: The go-to service for managing IoT devices on AWS.
- SSH Key Management: Use tools like ssh-keygen to manage your key pairs securely.
- Monitoring Tools: Services like CloudWatch can help you keep an eye on your devices and logs.
These tools will make your life a whole lot easier when managing IoT devices.
Real-World Examples of IoT SSH on AWS
Let’s look at a couple of real-world examples to see how SSH on AWS is being used for IoT devices:
Example 1: Smart Home Automation
Imagine a smart home system where all your devices are connected via AWS. You can remotely control your lights, thermostat, and security cameras using SSH. Not only is it convenient, but it’s also super secure.
Example 2: Industrial Sensors
In industrial settings, SSH on AWS can be used to monitor and manage thousands of sensors. This allows companies to collect valuable data and make informed decisions in real-time.
These examples show just how versatile and powerful SSH on AWS can be.
Wrapping It All Up
Accessing IoT devices through SSH on AWS is a game-changer for secure device management. From setting up your first EC2 instance to implementing best security practices, this guide has covered everything you need to know.
Remember, security should always be your top priority. Keep your devices updated, monitor your logs, and limit access to only those who need it. And don’t forget to plan for scalability as your network grows.
Now it’s your turn. Take what you’ve learned and start managing your IoT devices like a pro. Leave a comment below if you have any questions or share this article with your friends. Together, let’s make the IoT world a safer and more connected place!